Log Manager 101
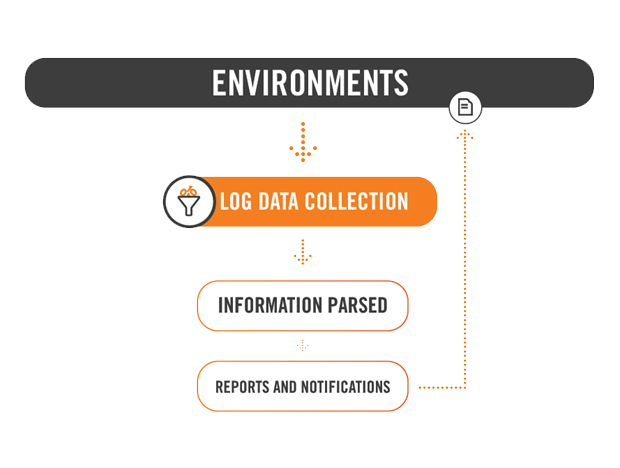
Alert Logic Log Manager is a log management solution that is delivered using a software-as-a-service (SaaS) model that works across any combination of Amazon Web Services, Microsoft Azure, and On-Premise data centers. In addition, Log Manager is a powerful security platform that can help a company detect and research intrusions and security breaches for ongoing security improvements. With Log Manager, you get automated log collection, storage, reporting, correlation and alerting across your entire environment.
Key Benefits
- Meet compliance requirements for log management, such as PCI, HIPAA, and others
- Increase IT security posture with greater visibility into asset activity via log message data
- Collect logs from Amazon Web Services, Microsoft Azure, and On-Premise data centers
- Safely store log data in our SSAE 16 Type 2 verified, redundant data centers
- Numerous out-of-the-box reports and dashboards
- Cloud-powered infrastructure provides powerful search, analysis and forensic capabilities
- Correlate events, set automatic Alerts, and schedule reoccurring reports
Additional services
Alert Logic offers two additional services that leverage the Log Manager platform.
LogReview
Log Review delivers a powerful compliance service where certified security analysts monitor compliance events on a daily basis, helping companies meet with demanding compliance standards.
ActiveWatch
ActiveWatch Services implements a superior approach to log management and security issue identification that provides near real-time deep insight and continuous protection at an affordable cost.
Log Manager is part of Cloud Defender
Cloud Defender provides you with our entire suite of security products. This includes Log Manager, Threat Manager, and Web Security Manager. This holistic solution is delivered through our Security-as-a-Service (SaaS) model and provides a fully managed, integrated security package.
Cloud Defender components
- Log Manager
- Threat Manager is an intrusion detection system (IDS) and vulnerability scanner.
- Web Security Manager is an out-of-band web application firewall (WAF) that monitors your web traffic and logs web violations but does not block requests.
Log Manager Architecture
Log Manager provides multiple methods for collecting log data within a customer's environment; agentless for cloud services, universal agents, remote collector, virtual appliance, and a dedicated Alert Logic appliance. These methods can be mixed and matched as needed across Amazon Web Services, Microsoft Azure, and On-Premise data centers.
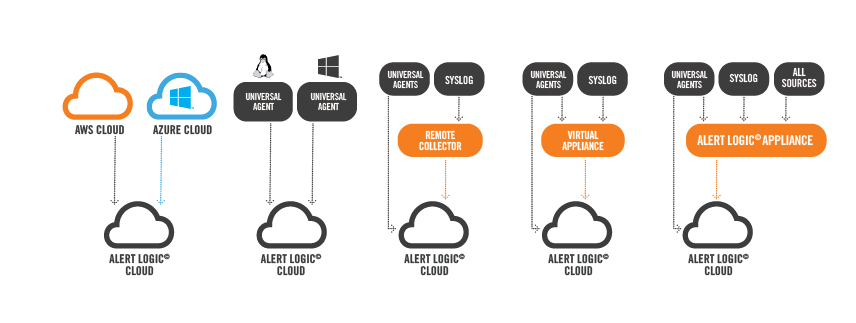
Universal Agents: Alert Logic agents support Windows and Unix/Linux operating systems and can be configured for Syslog, Windows Event logs, and Flat File log collection. The agent collects, compresses, and encrypts the log data and then securely sends it to the Alert Logic cloud. Agents also collect host metadata for presentation in the Alert Logic console and are able to report on collection status, statistics, and history. The agents run at a low priority, are light on resources, and upgrade automatically by default. Alert Logic agents also support log collection from auto-scaling instances (often found in Public Cloud environments).
Remote Collector: Log Manager Remote Collectors collect and forward Syslog data to the Alert Logic cloud, and are ideal for collecting Syslog data from network devices/firewalls, which cannot run an agent, and VMware is not available for the virtual appliance. They can be installed on either a Windows or Linux machine, are remotely upgradeable, and do not require a virtual VMware instance (as does the Virtual Appliance). Syslog data is compressed and encrypted prior to sending. The remote collector will upgrade automatically by default.
Virtual Appliance: The Log Manager virtual appliance collects and forwards Syslog data to the Alert Logic cloud. Although similar in function to the remote collector (Syslog collection from devices which cannot run an Agent), the virtual appliance must be installed within a VMware virtual machine. Virtual appliances can also provide a single point of network egress for the universal agent. The appliances are fully managed by Alert Logic, including all software components on the appliance.
Physical Appliance: Log Manager also offers a dedicated physical 1U log collection appliance. The physical appliance is able to collect Windows, Syslog, and Flat File logs without universal agents, also called remote collection; it can act as a single point of network egress for the universal agents, and it can provide dedicated compute resources for log collection. Best used for environments where collection agents are not desired and/or have high log volumes. The appliances are fully managed by Alert Logic, including all hardware and software components on the appliance.
Log Manager concepts
|
Host: A Log Host is a representation within the Alert Logic console of an installed universal agent, virtual appliance, or physical appliance. |
|
Source: A log source is a software or hardware component that produces log data. There are multiple types of sources and multiple methods of getting log data from the sources. The types of sources supported by Log Manager are Syslog, Windows Event Log, Flat Files, as well as various cloud services from Amazon Web Services and Microsoft Azure. |
|
Collectors: Collectors are hardware or software components that collect or receive log data from log sources. Collectors can be physical appliances, virtual appliances or remote collector agents that run on non-dedicated hosts. |
|
Credentials: A credential is the information required for Log Manager to authenticate itself to a log source in order to collect log data. A credential can be applied for each source as required and can be composed of a username and password or whatever other authentication details are required for that specific source. Credentials are only used for cloud native collection and remote (appliance based) Windows Event Log and remote Flat File collection. |
|
Policies: Alert Logic allows you to create three types of policies in Log Manager: Collection Policies, Correlation Policies, and Update Policies.
|
|
Alert Rules: Alert Logic allows you to create two types of alert rules for Log Manager to receive important notifications. The purpose of an Alert Rule is to produce an email notification based on a specific outcome. These include Collection and Correlation.
|
|
Saved Views: Saved Views allows you to instantly save a search query that you have created so that you can run the saved view at any time in the future without having to recreate the entire search query itself. |
| Scheduled saved views: Saved views can be scheduled to run at predetermined times or on a reoccurring basis. They also can be scheduled to run immediately, so that the user doesn’t have to wait on a search query to return a large result set. These reports can be used as part of a user defined process to review logs regularly. |
|
Parser: A log parser is an internal component of Log Manager that helps identify and extract data from logs collected from defined sources. All data from log sources can be collected by Log Manager, but to use all the searching, reporting, correlation and alerting functionality the log data must be parsed. Log Manager includes thousands of parsers and new parsers are added frequently. Parsers can be requested for any log messages that are not being parsed. |
Sample Log Manager workflow
The following scenario shows you a typical workflow for Alert Logic Log Manager.
A Security Analyst wants to use Log Manager to produce a daily report showing all failed logins to several critical Windows servers in their environment.
- The Security Analyst installs the Alert Logic agent on the critical Windows servers in their environment.
Note: The analyst can also install an Alert Logic physical appliance to collect the windows event logs remotely.
- The Analyst then logs into the Alert Logic console to view the Windows server hosts. In the Alert Logic console they will configure the Windows Event Log sources.
- Within 15 minutes of being configured, Alert Logic will collect the Windows Event logs, encrypt the data, and send it to the Alert Logic cloud.
- The Alert Logic cloud will parse each log message and safely store log data in our SSAE 16 Type 2 verified, redundant data centers
- The Analyst will then log in to Alert Logic console and create a search query for failed login attempts. The query results in a detailed report. They can adjust the query report, filtering for specific fields of interest and applying additional criteria. They can then do the following:
- Save their search query and run the query on a daily basis.
- Send the report automatically as an email.
- Export the report to CSV or PDF.