Threat Manager detection
After you create an assignment policy and update a protected host in Threat Manager, you can design a customized detection system that best suits your goals.

Updating or deleting detection or policy configurations affects all interconnected configurations.
Hosts
Hosts are uniquely identifiable devices registered internally in the Alert Logic console.
Create a protected host for a threat host
Protected hosts are uniquely identifiable devices registered externally from the Alert Logic console. To create a protected host for a threat host, the threat host must be online. If you do not see an option to create a protected host, the threat host is offline. To sort the list of threat hosts by online status, in the Status column, click Status.
To create a protected host source for a threat host:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- In the threat hosts table, in the Actions column, click the plus icon (
 ).
). - See the table below for field definitions and fill in the form.
- Click Save.
Create a protected host form
| Field/Option | Description | Sample Value |
Visible |
|---|---|---|---|
| Source Name | Name of this source. It will show on the display list and other areas of this product. | Server-tmdocs | Always |
| Use an existing Assignment Policy | Select this option to choose a policy from the existing Assignment Policy list. | Not applicable | Always |
| Create a new Assignment Policy | Select this option to open the Create a new Assignment Policy section. | Not applicable | Always |
| Existing Assignment Policy list | Select a policy from this list to assign it to the protected host. | cali-ngtm-01 Assignment | Visible when Use an existing Assignment Policy is selected. |
|
Create new Assignment Policy mini-form Visible when you select Create new Assignment Policy |
|||
| Field/Option | Description | Sample Value |
Visible |
| Appliance Assignment Policy Name | Policy name. This name will be added to the Existing Assignment Policy list. | cali-ngtm-01 Assignment | Visible when Create a new Assignment Policy is selected. |
| Appliances/ Secondary Appliances |
An appliance on your network. | i-27273bcb | Visible when Create a new Assignment Policy is selected. |
| Restrict Network | Select this option if you want to include a netmask. | Not applicable | Visible when Create a new Assignment Policy is selected. |
| Netmask | One CIDR address. | 10.0.0.0/16; partial address specifications are not acceptable. | Visible when Create a new Assignment Policy is selected. |
| Use existing Whitelist Policies | Select this option to choose a policy from the Existing Whitelist Policy list. | Not applicable | Visible when Create a new Assignment Policy is selected. |
| Create a new Whitelist Policy | Select this option to open the Create a new Whitelist Policy section. | Not applicable | Visible when Create a new Assignment Policy is selected. |
| Existing Whitelist Policy list | Select a policy from this list to assign it to the protected host. | SF01183529 Pentest | Visible when Create a new Assignment Policy and Use existing Whitelist Policies is selected. |
|
Create new Whitelist Policy mini-form Visible when you select Create new Assignment Policy and Create a new Whitelist Policy |
|||
| Field/Option | Description | Sample Value |
Visible |
| Name | Policy name. This name will be added to the Existing Whitelist Policy list. | SF01183529 Pentest | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Enabled | Select this option to activate the policy. | Not applicable | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Rules | Click  to add rules to the Whitelist Policy. This includes Protocol, CIDR, and Port. to add rules to the Whitelist Policy. This includes Protocol, CIDR, and Port. |
Not applicable | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Protocol | Select the internet protocol for the current rule. | tcp | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| CIDR | Type the Classless Inter-Domain Routing address for the current rule. | 10.0.0.0/16 | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Port | Type the port for the current rule. | 22 | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Field/Option | Description | Sample Value |
Visible |
| Use existing Host Policies | Select this option to choose a policy from the Existing Host Policy list. | Not applicable | Always |
| Create new Host Policy | Select this option to open the Create a new Host Policy section. | Not applicable | Always |
| Existing Host Policy list | Select a policy from this list to assign it to the protected host. | Default-test | Visible when Use existing Host Policies is selected. |
|
Create new Host Policy mini-form Visible when you select Create new Host Policy |
|||
| Field/Option | Description | Sample Value |
Visible |
| Name | Policy name. This name will be added to the Existing Host Policy list. | Default-test | Visible when you select Create new Host Policy. |
| Encrypt | Select this option to encrypt traffic from the agent to the appliance. | Not applicable | Visible when you select Create new Host Policy. |
| Tags | A tag is a customer defined identifier that can be assigned to one or more sources. A customer can use tags to organize or search for specific types of sources. | High usage | Always |
View threat hosts
To view threat hosts:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- Place your cursor over the desired threat host and click view.
- Select one of the following tabs to view information about the threat host:
- Host Details

The Status field indicates if a host is online or offline. If a host is offline, you cannot create a new protected host.
- Metadata History
- Status History
Edit an updates policy for a threat host

Updating detection or policy configurations affects all interconnected configurations.
To edit an updates policy for a threat host:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- In the table of threat hosts, in the Actions column, click the pencil icon (
 ).
). - In the Host Name field, enter a descriptive name.
- Select or create an updates policy as follows:
- Keep the default selection: Use existing Updates.
- From Existing Updates, select an updates policy.
- Select Create new Updates.
- In the Updates Name field, type a descriptive name.
- In Updates Frequency, select one of the following:
- Automatic
- Scheduled
- Never
- If prompted, specify your scan options.

Use 24 hour format to schedule updates.
- In the Tags field, type an easily filtered tag.
- Click Update.
Mass edit threat hosts
Mass edit provides the option to edit the updates policies and tags for all the threat hosts, filtered threat hosts, or specific threat hosts you select. Also, mass edit contains a mass archive feature.

If the archive feature issues an Internal Server Error, edit the threat host to make the object valid.

If the restore feature is unavailable, edit the threat host to make the object valid.
To mass edit all threat hosts:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- In the threat hosts table, in the Actions column, click the gear icon (
 ).
). - Select Mass Edit.
- In Apply changes to, select All Hosts.
- In Updates, select the updates policy to use.
- From Tags, select a tag option, and then in the Tags field, enter the applicable tag(s).
- From Archive Hosts, select an option.

If the restore feature is unavailable, edit the threat host to make the object valid.
- Click Apply.
To mass edit only filtered threat hosts:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- In Select Some Options, click the field, select a filter, and then click Apply filters.
- In the threat hosts table, in the Actions column, click the gear icon (
 ).
). - Select Mass Edit.
- In Apply changes to, select Only Filtered Hosts.
- In Updates, select the updates policy to use.
- From Tags, select a tag option, and then in the Tags field, enter the applicable tag(s).
- In Archive Hosts, select an option from the drop-down menu.

If the restore feature is unavailable, edit the threat host to make the object valid.
- Click Apply.
To mass edit only selected threat hosts:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- In the Actions column, click the gear icon (
 ).
). - Select Mass Edit.
- In Apply changes to, select Only Selected Hosts.
- Below the configuration area, select the threat hosts to edit.
- In Updates, select the updates policy to use.
- From Tags, select a tag option, and then in the Tags field, enter the applicable tag(s).
- From Archive Hosts, select an option.

If the restore feature is unavailable, edit the threat host to make the object valid.
- Click Apply.
Archive a threat host
Archive a threat host to visibly remove the log host entry from the Alert Logic console.
To archive a threat host:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- Place your cursor over the desired threat host and click the box icon (
 ).
).
- Click Archive.

If the archive feature issues an Internal Server Error, edit the threat host and remove any current assignment policy that the Protected Host has to allow this host to be archived.
Restore an archived threat host
To restore an archived log host:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Hosts.
- Above the threat hosts table, click the box icon labeled Show Archived (
 ).
). - Place your cursor over the desired threat host and click restore (
 ).
). - Click Restore.

If the restore feature is unavailable, edit the threat host to make the object valid.
Protected hosts
Update a protected host
Threat Manager allows you to update your protected hosts.
To update a protected host:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Protected Hosts.
- In the table of protected hosts, select the protected host you want to update, and then click the pencil icon (
 ).
). - Fill in the form and click Update. See the table below for field definitions.
Update a protected host form
| Field/Option | Description | Sample Value |
Visible |
|---|---|---|---|
| Source Name | Name of this source. It will show on the display list and other areas of this product. | Server-tmdocs | Always |
| Use an existing Assignment Policy | Select this option to choose a policy from the existing Assignment Policy list. | Not applicable | Always |
| Create a new Assignment Policy | Select this option to open the Create a new Assignment Policy section. | Not applicable | Always |
| Existing Assignment Policy list | Select a policy from this list to assign it to the protected host. | cali-ngtm-01 Assignment | Visible when Use an existing Assignment Policy is selected. |
|
Create new Assignment Policy mini-form Visible when you select Create new Assignment Policy |
|||
| Field/Option | Description | Sample Value |
Visible |
| Appliance Assignment Policy Name | Policy name. This name will be added to the Existing Assignment Policy list. | cali-ngtm-01 Assignment | Visible when Create a new Assignment Policy is selected. |
| Appliances/ Secondary Appliances |
An appliance on your network. | i-27273bcb | Visible when Create a new Assignment Policy is selected. |
| Restrict Network | Select this option if you want to include a netmask. | Not applicable | Visible when Create a new Assignment Policy is selected. |
| Netmask | One CIDR address. | 10.0.0.0/16; partial address specifications are not acceptable. | Visible when Create a new Assignment Policy is selected. |
| Use existing Whitelist Policies | Select this option to choose a policy from the Existing Whitelist Policy list. | Not applicable | Visible when Create a new Assignment Policy is selected. |
| Create a new Whitelist Policy | Select this option to open the Create a new Whitelist Policy section. | Not applicable | Visible when Create a new Assignment Policy is selected. |
| Existing Whitelist Policy list | Select a policy from this list to assign it to the protected host. | SF01183529 Pentest | Visible when Create a new Assignment Policy and Use existing Whitelist Policies is selected. |
|
Create new Whitelist Policy mini-form Visible when you select Create new Assignment Policy and Create a new Whitelist Policy |
|||
| Field/Option | Description | Sample Value |
Visible |
| Name | Policy name. This name will be added to the Existing Whitelist Policy list. | SF01183529 Pentest | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Enabled | Select this option to activate the policy. | Not applicable | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Rules | Click  to add rules to the Whitelist Policy. This includes Protocol, CIDR, and Port. to add rules to the Whitelist Policy. This includes Protocol, CIDR, and Port. |
Not applicable | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Protocol | Select the internet protocol for the current rule. | tcp | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| CIDR | Type the Classless Inter-Domain Routing address for the current rule. | 10.0.0.0/16 | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Port | Type the port for the current rule. | 22 | Visible when you select Create new Assignment Policy and Create a new Whitelist Policy. |
| Field/Option | Description | Sample Value |
Visible |
| Use existing Host Policies | Select this option to choose a policy from the Existing Host Policy list. | Not applicable | Always |
| Create new Host Policy | Select this option to open the Create a new Host Policy section. | Not applicable | Always |
| Existing Host Policy list | Select a policy from this list to assign it to the protected host. | Default-test | Visible when Use existing Host Policies is selected. |
|
Create new Host Policy mini-form Visible when you select Create new Host Policy |
|||
| Field/Option | Description | Sample Value |
Visible |
| Name | Policy name. This name will be added to the Existing Host Policy list. | Default-test | Visible when you select Create new Host Policy. |
| Encrypt | Select this option to encrypt traffic from the agent to the appliance. | Not applicable | Visible when you select Create new Host Policy. |
| Tags | A tag is a customer defined identifier that can be assigned to one or more sources. A customer can use tags to organize or search for specific types of sources. | High usage | Always |
Mass edit protected hosts
The Threat Manager mass edit feature allows you to simultaneously perform the same edits on one or more protected hosts.
To mass edit protected hosts:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Protected Hosts.
- In the table of protected hosts, in the Actions column, click the gear icon (
 ).
). - Select Mass Edit. A configuration area expands on your screen.
- Make the following changes if applicable:
- Specify the hosts to which you want to apply changes:
- All hosts
- Only filtered hosts
- Only selected hosts
- Specify an appliance assignment policy.
- Select which, if any, host policy setting to change.
- Specify one of the following tag settings:
- Do not change tag settings
- Append additional tags to these networks—Type tags you want added to the networks.
- Replace existing tags on these networks—Type tags you want to replace those associated with the networks.
- Remove specific tags from these networks—Type the tags you no longer want associated with the networks.
- Remove all tags from these networks
- Specify the hosts to which you want to apply changes:
- Select whether to delete the selected hosts.

You cannot undo this action.
- Click Apply.
Export protected hosts
Threat Manager allows you to export your list of protected hosts to a file. You can choose one of the following formats for the exported file:
- Comma separated values (.csv)
- Tab delimited values (.txt)
- Microsoft Excel 1997–2003 (.xls)
- Microsoft Excel 2007 (.xlsx)
To export protected hosts:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Protected Hosts.
- In the table of protected hosts, in the Actions column, click the gear icon (
 ), and then select Export Protected Hosts.
), and then select Export Protected Hosts. - Select a file format for the exported file.
- Click Download.
Archive and restore protected threat hosts
To safeguard against permanent loss of data, Threat Manager provides the archive and restore features. To archive a threat host, you must delete all protected hosts data streams associated with the threat host.

If the archive feature issues an Internal Server Error, edit the threat host to make the object valid, and then in the left navigation area, under Detection, click Protected Hosts. Next, you must delete any protected hosts associated with the threat host.

If the restore feature is unavailable, edit the threat host to make the object valid.
Delete a protected host
Threat Manager allows you to remove existing protected hosts.
To delete a protected host:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Protected Hosts.
- In the table of protected hosts, select the protected host you want to delete, and then click the trash icon (
 ).
). - Click Delete.
Appliances
Update an appliance
Threat Manager allows you to edit and update existing appliance configurations.
To update an appliance:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Appliances.
- In the table of appliances, within the corresponding row, click the pencil icon (
 ).
). - In the Appliance Name box, enter an appliance name.
You can perform the following edits to the appliance configuration:
Use an existing whitelist policy
- Select Use existing Whitelist Policies.
- From the existing Whitelist Policy drop-down menu, select a whitelist policy.

If you do not want to assign a whitelist policy to this appliance, select No Whitelist Policy.
Create a new whitelist policy
- Select Create a new Whitelist Policy.
- In the Name box, enter a descriptive name.
- Create one or more rules by entering information for the following fields:
- Protocol
- CIDR
- Port
Enable vulnerability scanning
- Select Enable Scans.

Enabling scans affects performance. Enabling scanning on devices with fewer than four cores may result in degraded performance of the Threat Manager device.
Assign tags
- Enter tag(s) in the Tags box.
- Click Update.

Updating detection or policy configurations affects all interconnected configurations.
Mass edit appliances
Threat Manager allows you to simultaneously apply edits to multiple existing appliances.
To mass edit appliances:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Appliances.
- In the table of appliances, in the Actions column, click the gear icon (
 ).
). - Select Mass Edit to display a configuration area.
- Select the appliances to apply changes.

To apply changes to only selected appliances, then select those appliances.
- Select which, if any, appliance tag settings to change.
- To assign tags, enter tags in the Tags box.
- Select whether to delete the selected appliances.

You cannot undo this action.
- Click Apply.
Export appliances
Threat Manager allows you to export existing appliances to a variety of file formats. You can choose one of the following formats for the exported file:
- Comma separated values (.csv)
- Tab delimited values (.txt)
- Microsoft Excel 1997–2003 (.xls)
- Microsoft Excel 2007 (.xlsx)
To export appliances:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Appliances.
- In the table of appliances, in the Actions column, click the gear icon (
 ).
). - Select Export Appliances to display a configuration area.
- Select a file format.
- Click Download.
Enable scans
Threat Manager allows you to run internal vulnerability scans from the Alert Logic appliance in your environment. This feature allows you to enable and disable internal scanning from the appliance interface.
For more information about scans, see Scans.
To enable scans:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Appliances.
- In the table of appliances, within the corresponding appliance row, click the pencil icon (
 ).
). - Select Enable Scans.
- Click Update.
Effects on performance
Enabling scans can affect the performance of your appliance, depending on the number of cores in your environment. The following table illustrates the effect on performance.
| Number of cores | Performance impact |
|---|---|
| 4* | 50% |
| 8 | 17% |
| 16 | 7% |
| * Minimum required number of cores. | |
Networks
A Threat Manager network is a range of IP addresses, expressed in CIDR notation, that you want to monitor within your network. A Threat Manager network cannot monitor a range of IP addresses larger than a /8 CIDR.
To monitor a Threat Manager network, you must apply the network to a monitoring policy. You may apply multiple networks to a monitoring policy. For more information about monitoring policies, see Monitoring policies.
Create and protect networks
The Threat Manager networks feature allows you to create and protect networks.
To create and protect a network:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Networks.
- In the table of networks, in the Actions column, click the gear icon (
 ), and then select Protect Networks.
), and then select Protect Networks. - In the Name box, type a name for the network.
- In the CIDR box, type the network CIDR information.
- To assign tags to your network, in the Tags box, type one or more tags.
- To monitor the network immediately, select the appliance that you want to monitor the network.
- Click Save.
If you do not select an appliance, the configuration status of your network appears as "unprotected." To protect this network at a later time, you must assign it to a monitoring policy, and then assign the monitoring policy to an appliance. For more information about monitoring policies, see Monitoring policies.
Edit networks
The Threat Manager edit feature allows you to perform edits on one or more networks.
To edit networks
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Networks.
- In the table of networks, in the Actions column, hover on the network that you want to edit and click the pencil icon (
 ).
). - Make necessary edits to the following fields:
- Name
- CIDR
- Collection Alerts
- Tags
- Click Update.
Mass edit networks
The Threat Manager mass edit feature allows you to simultaneously perform the same edits on one or more networks.
To mass edit networks:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Networks.
- In the table of networks, in the Actions column, click the gear icon (
 ), and then select Mass Edit.
), and then select Mass Edit. - Make the following changes, if applicable:
- Specify whether you want changes applied to the following:
- All Networks
- Only Filtered Networks
- Only Selected Networks
- Select an appliance to protect the specified networks.
- Select one of the following tag settings:
- Do not change tag settings
- Append additional tags to these networks
Type tags you want added to the networks. - Replace existing tags on these networks
Type tags you want to replace those associated with the networks. - Remove specific tags from these networks
Type the tags you no longer want associated with the networks. - Remove all tags from these networks
- Specify whether you want to delete the selected networks.
- Specify whether you want changes applied to the following:
- Click Apply.
Force statistics update
The Networks feature allows you to view the details for the networks you create. Threat Manager automatically updates the displayed information and statistics every 30 minutes. You can manually force a statistics update to refresh the network screen display.
To force a statistics update:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Networks.
- In the table of networks, in the Actions column, click the gear icon (
 ), and then select Force Statistics Update.
), and then select Force Statistics Update.
Export networks
Threat Manager allows you to export your list of networks to a file. You can choose one of the following formats for the exported file:
- Comma separated values (.csv)
- Tab delimited values (.txt)
- Microsoft Excel 1997–2003 (.xls)
- Microsoft Excel 2007 (.xlsx)
To export networks:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Networks.
- In the table of networks, in the Actions column, click the gear icon (
 ), and then select Export Networks.
), and then select Export Networks. - Select a format for the exported file.
- Click Download.
Delete a network
Threat Manager allows you to remove a network.
To delete a network:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Networks.
- Select the table view.
- In the table of networks, select a network, and then click the trash icon (
 ).
). - Click Delete.
Certificates, keys, and SSL decryptor
If you enable Secure Sockets Layer (SSL) entitlement for your Alert Logic account, you can create certificates, which Threat Manager automatically assigns to your appliances.
To use this feature, you must enable SSL entitlement for your account, and you must have permission to manage certificates and keys.
To access Certificates and Keys:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Certificates & Keys.

If you do not see the Certificates & Keys section in the user interface, you do not have access to this feature.
To use this feature, contact Alert Logic by e-mail at support@alertlogic.com or by phone (US: (877) 484-8383, UK: +44 (0) 203 011 5533).
SSL certificates and keys
SSL is the standard mechanism used to secure communication on the web, and SSL helps secure information, such as credit card numbers, personal information, and private data. At the most basic level, an SSL-enabled web server uses certificates and private keys to establish a secure and encrypted connection with web browsers.
The private key is the necessary component to decrypt the entire SSL connection. Guard the private key as carefully as a password. Alert Logic uses an industry-standard key encryption mechanism to store private keys.
A certificate matches a key, and the certificate provides authenticated identity information to web browsers and other client software. Certificates present authentication information during the establishment of a secure SSL connection, so certificates are considered public information.
Threat Manager allows you to upload your SSL certificate and corresponding key. This action allows the SSL decryptor to decrypt traffic for further analysis.
Alert Logic SSL Decryptor
The Alert Logic SSL Decryptor extends the advanced intrusion detection capabilities of Threat Manager. The decryptor allows the appliance to inspect the encrypted SSL traffic.
Alert Logic SSL Decryptor Setup Requirements and Process
The SSL Decryptor setup process requires the following:
- A copy of the SSL certificate for the protected site exported to .PEM format without a passphrase.

When you upload certificates and private keys to the Alert Logic console, you provide a secure and encrypted communication between your web browser and Alert Logic servers. In addition, Alert Logic stores private keys through an industry-standard key encryption mechanism. Because Alert Logic software handles the key automatically and securely, you need not upload the private key with a passphrase. If you previously saved your unencrypted private key to a file, Alert Logic strongly recommends you destroy the key immediately after you upload the key.
- The TCP/IP address and port on your system that you want to monitor, and that you associated with your SSL certificate. For example, 10.10.10.17 is your IP address on port 443.
Maintenance of the SSL decryption on the Threat Manager appliance
The Alert Logic SSL Decryptor requires the SSL certificate information to detect possible intrusions in encrypted channels. SSL certificates expire. A renewed SSL certificate requires an update to the certificate information in the Alert Logic console.

Alert Logic does not support any cipher that uses Diffie-Hellman key exchange protocols. This includes the use of Perfect Forward Secrecy (PFS).

If you change the certificate for a protected device, but do not change the certificate SSL Decryptor, the Decryptor cannot examine SSL traffic for that site.
Add a certificate
To inspect SSL-encrypted traffic, you must upload a certificate through the Alert Logic console. After you add a certificate, it will automatically be assigned to all appliances.

Alert Logic does not support any cipher that uses Diffie-Hellman key exchange protocols. This includes the use of Perfect Forward Secrecy (PFS).
To add a certificate:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Certificates & Keys.
- In the table of certificates, in the Actions column, click the gear icon (
 ).
). - Select Add Certificate.
-
Complete the fields with the appropriate information:
- Name—A descriptive name to identify the certificate.
- Certificate Content—The PEM-encoded certificate.
This field must include the header and footer notes. - Private Key Content—The PEM-encoded private key.
This field must include the header and footer notes.
The PEM-encoded private key must be in RSA format, or you must convert the key to RSA format.

Correct format for the Add Certificate page
- Include "----BEGIN RSA PRIVATE KEY----" and "----END RSA PRIVATE KEY----" in Private Key Content.
- Include "----BEGIN CERTIFICATE----" and "----END CERTIFICATE----" in Certificate Content.
The following shows an example of valid certificate format:
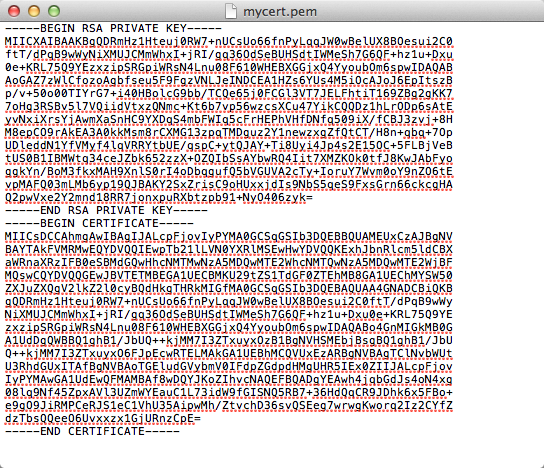

You can upload a PEM file instead of completing the empty fields. To upload a PEM file, click Browse in the PEM File Upload field and then search for and select the desired PEM file.
Your PEM file must have both certificate information and private key information.
- Click Save.

Allow about 15 minutes for your system to update with these changes.
View certificate information
Threat Manager allows you to view information for public certificates. Alert Logic protects confidential private keys, so you cannot retrieve or view private keys.
To view information about a certificate:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Certificates & Keys.
- In the table of certificates, within the corresponding row, place your cursor in the Actions column.
- Click View.
Information, which includes the name of the certificate, the host IP address, the host port, and the certificate key, appears on the right side of the screen.
Delete a certificate
Threat Manager allows you to delete uploaded certificates.
When you delete a certificate, you delete the corresponding key, which means Alert Logic can no longer decrypt the SSL-encrypted traffic associated with the deleted certificate and private key.
To delete a certificate:
- At the top of the Alert Logic console, from the drop-down menu, click Threat Manager.
- In the left navigation area, under Detection, click Certificates & Keys.
- In the table of certificates, within the corresponding row, place your cursor under the Actions column and click the trash icon (
 ).
). - Click Delete.

Allow about 15 minutes for your system to update with these changes.